Last updated: May 27, 2020 at 4:06 PM
Last updated: May 27, 2020 at 4:06 PM
Last month, a cross-site scripting vulnerability was discovered in WordPress, the site's platform.
Therefore, from April 22 to 28, we have updated wordpress4.1.2/4.2/4.2.1, which was released for security protection.
Along with that, wordpress problems also occur, such as reporting to the Forum of WordPress, I have also encountered a variety of troublesome work.
In the meantime, as if they had had the opportunity, we received a furious attack from a legion of hackers on our site.
In the end, i couldn't afford to write a blog last month because i needed to take that measure.
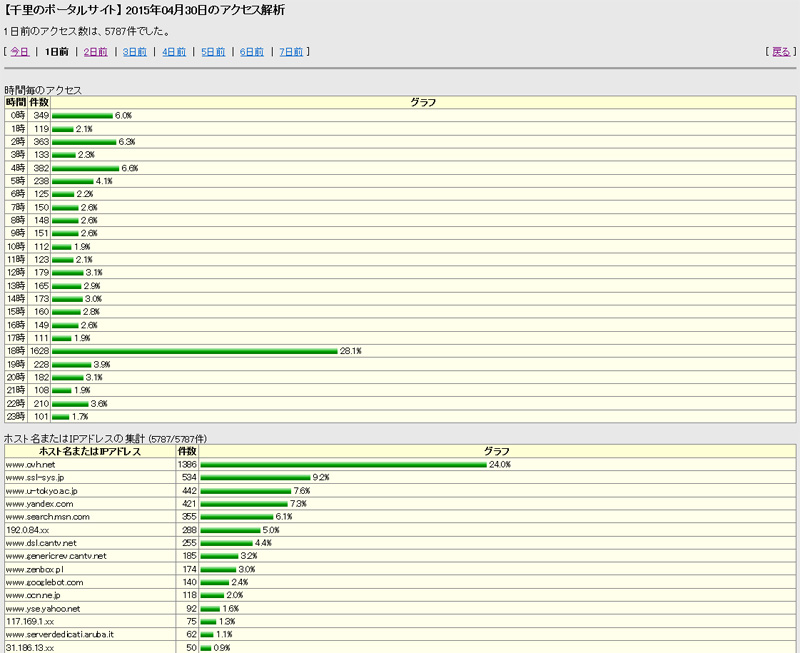
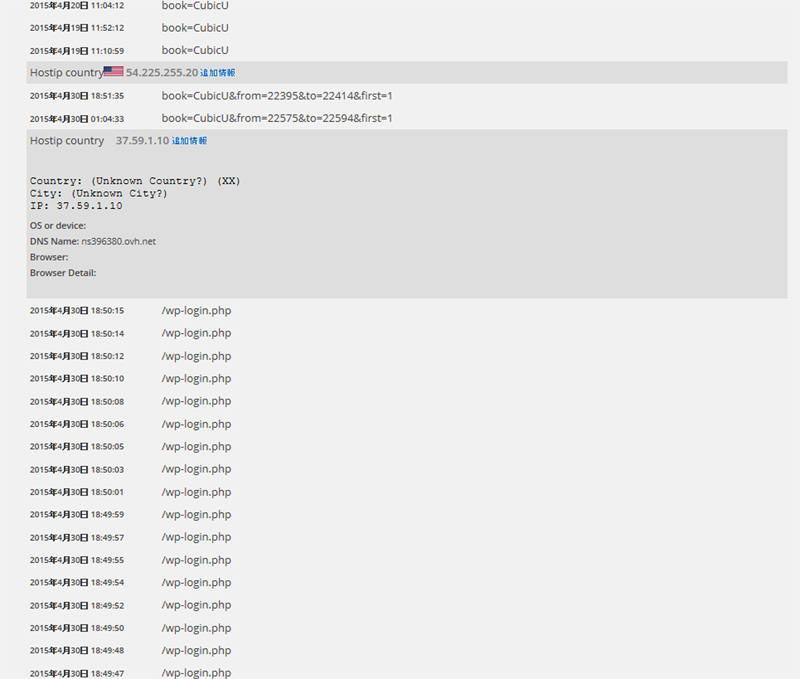
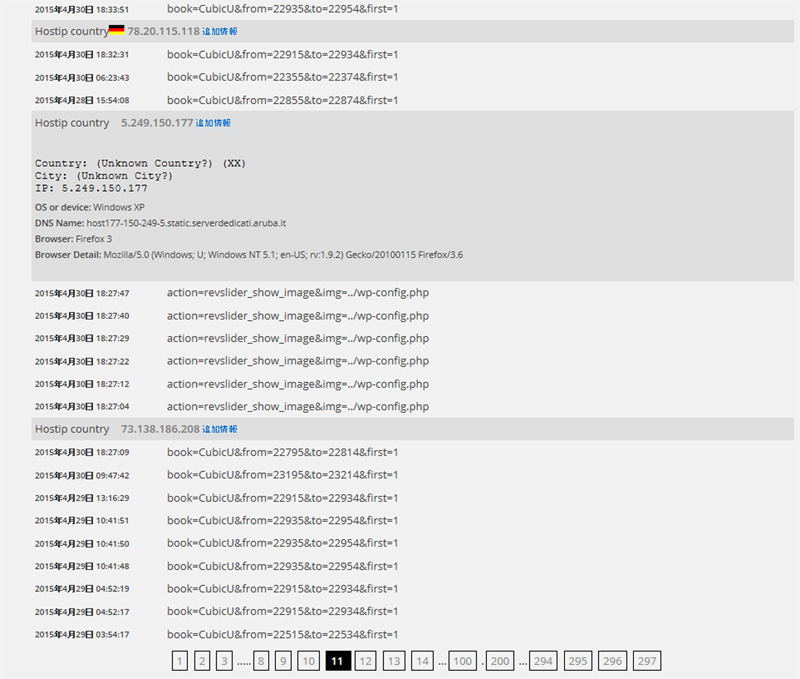
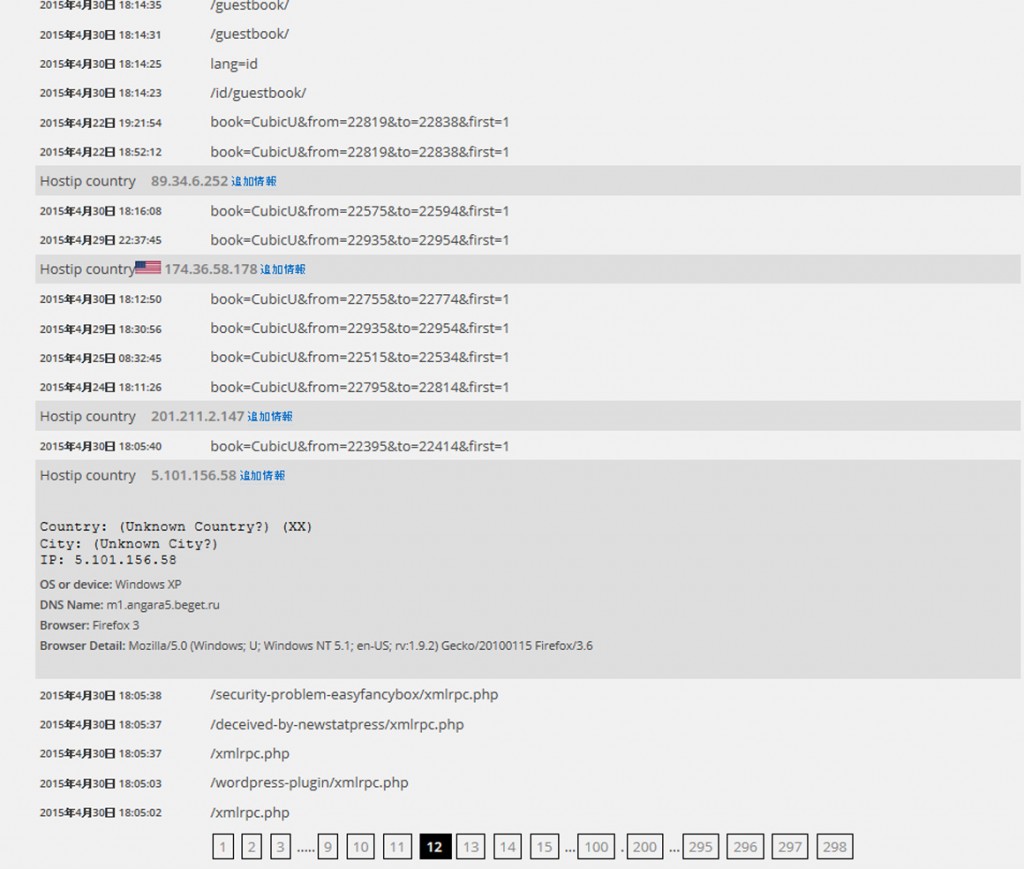
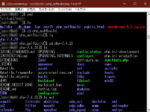
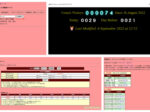
The first attached photo is the screen of perl's monitoring program, which detects 1628 accesses at 18.
NewStatPress logs revealed that the access source of "ns396380.ovh.net" was a brute force attack from France targeting wp-login.php.
However, the most common attacks are attacks on malformed writing (SPAM) in the comment field and the plugin RevSlider, which is known to be vulnerable in earlier versions. In addition, via xmlrpc.php, password hacking and pingback attacks (DDoS attacks) are also checked from the access log.
The majority of attacks originated from PCs (windows XP) and websites that were hijacked by hackers via viruses and malware.
Organized hacking seems to be very common from Russia and Ukraine.
Those software seems to be remotely controlled by some bad guys.
If brute force attacks are left unchecked, passwords may be decrypted, servers may be hijacked, resources may be exhausted, and servers will go down, so all of those IP addresses are currently blocked.
WordPress, anyone can easily build a blog site for free, because it has a rich plug-in, but it is the cms most users in the world, on the other hand, we are always under attack from hackers.
The link below explains the history of the 2013 large-scale hacking of the rental server Lollipop.
Report on damage to user site tampering by third parties
More than 8000 WordPress sites have been hacked, the fact that HP has been tampered with was a really shocking event.
To protect yourself from hackers,
- Set the password to something strong.
- Make sure that permissions on important system files (wp-config.php/wp-login.php/admin-post.php/xmlrpc.php, etc.) are not accessible to or referenced by third parties, and cannot be rewritten.
- Keep the WordPress body and plug-ins up to date.
- Install security-related plug-ins.
- Do not neglect to monitor for suspicious access.
- Block access from hackers. 👉 Restrict access from malicious BOTS
Is it like this?
By the way, in order to prevent URL / wp-login.php from being redirected to the actual URL (URL / wordpress / wp-login.php), the following definition is added to fuctions.php.
remove_action( 'template_redirect', 'wp_redirect_admin_locations', 1000 );
And the permission of wp-config.php is set to 404. Actually, I want to set it to 400, but it is impossible in a domain king server environment because Apache has no ownership.
However, security is high because access from outside is considerably restricted.
(Another server I own can use telnet / SSH)
Well, rabbits are a lot of difficulties. (m_m)
You can check the following sites to see if your site has been compromised by malware and participated in attacks on other sites.
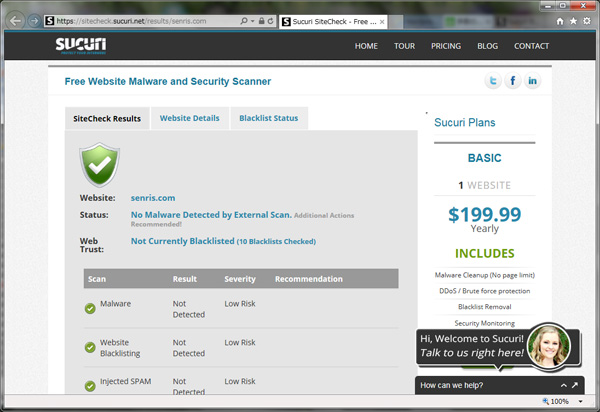
If a website is infected with a virus, it will be blacklisted and you will be penalized to be cut off from the Internet. So be careful!
* Added on May 8
The WordPress bug I pointed out was finally fixed with the release of 4.2.2.
👉 After updating to 4.1.2 / 4.2, browser freezes due to article update