Last updated: March 6, 2023 at 8:52 PM
Last updated: March 6, 2023 at 8:52 PM
* This page is constantly updated.
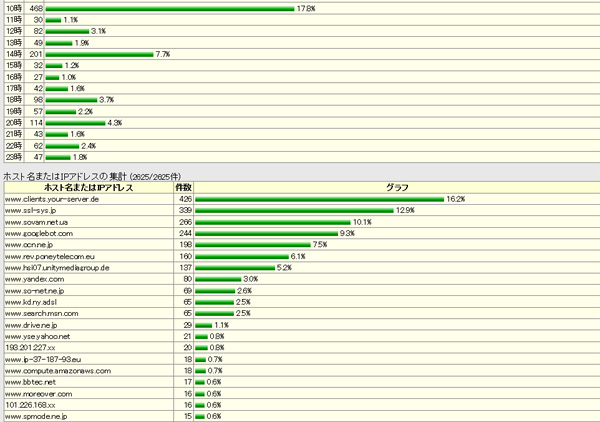
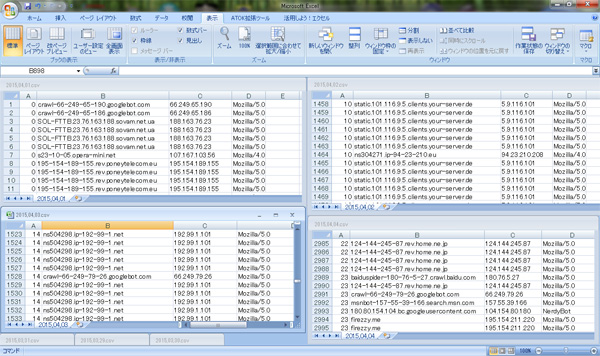
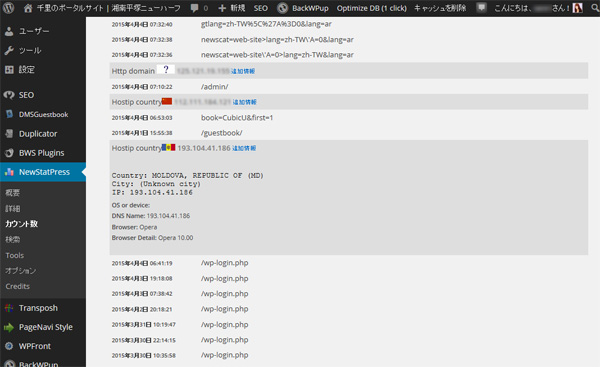
We investigated the results of the log of perl access analysis program sat on this site and the results of the WordPress plug-in "NewStatPress".
As a result, as usual, it was confirmed that there is a large amount of access from the annoying BOT that does not call itself BOT.
As for the BOT, we have confirmed the following types of information on this site.
(1) "SPAM BOT" to write the advertisement of the product to the bulletin board and the comment field randomly
⇒ All are guarded by "Google No CAPTCHA reCAPTCHA".
(2) "Hacking BOT" (Brute Force Attack) attempting to log in to WordPress
⇒ "Google No CAPTCHA reCAPTCHA" has all been guarded, and we have changed it to a strong password, so you'll be fine first.
* Added April 20
After that, as a result of further log analysis, we confirmed that there were many hacking sites that showed intrusion from the back door by sending the login name and password to xmlrpc.php of WordPress. Therefore, that IP address was blocked today.
(3) "hacking BOT" that attempts to rewrite articles by using vulnerabilities in plug-ins
⇒ The plug-in is not used on this site. In addition, this site has confirmed attacks on plug-ins such as "Revslider". ⇒ By browsing wp-config.php, they are trying to break into DBs and websites.
With regard to these attack sites, it is possible that PCs and websites with security vulnerabilities such as Windows XP and Windows 2000 have been infected with viruses, and these have been transformed into evil BOTs as a stepping stone.
Based on the above survey results, it is no longer possible to forgive malicious BOT behavior, so we have implemented a large-scale restriction on access to particularly malicious BOT.
The following is a part of the setting to deny access to this server added to ".htaccess" of Apache.
* As of April 10, 2018, a total of 441 IP addresses have been defined in ascending order.
# Denial of Access (Last modified - 2015/5/9)
order allow,deny
allow from all
deny from 144.76.0.0/16 # clients.your-server.de (Germany-SPAM)
deny from 148.251.0.0/16 # static.177.26.76.144.clients.your-server.de
deny from 5.9.146.29 # static.29.146.9.5.clients.your-server.de
deny from 94.23.40.23 # crawl15.lp.007ac9.net (your-server.de)
deny from 94.23.54.140 # France-Hacking site
deny from 94.23.59.161 # France-Hacking site
deny from 94.131.0.0/16 # AVK-NET (Russia-Hacking site)
deny from 193.104.41.0/24 # Moldova Hacking site (pinspb.ru Russia)
deny from 46.161.62.0/24 # Kazakhstan Network (pinspb.ru Russia-SPAM)
deny from 46.161.63.0/24 # Moldova Network (pinspb.ru Russia-SPAM)
deny from 195.154.0.0/17 # poneytelecom.eu (France-SPAM)
deny from 62.210.128.0/17 # 62-210-177-242.rev.poneytelecom.eu
deny from 213.186.33.0/24 # ip-198-27-82.net (France-SPAM)
deny from 37.187.0.0/16 # ns3371997.ip-37-187-93.eu (France-SPAM)
deny from 192.99.0.0/16 # ip-192-99-10.net (Canada-SPAM)
deny from 142.54.161.130 # Canada-SPAM
deny from 142.54.160.106 # Canada-SPAM
deny from 142.54.184.181 # Canada-SPAM
deny from 198.27.82.152 # ns4006763.ip-198-27-82.net (Canada-SPAM)
deny from 162.244.12.179 # US-SPAM
deny from 69.30.255.130 # US-SPAM
deny from 76.164.192.43 # US-SPAM
deny from 184.168.152.208 # US-Hacking Site
deny from 83.139.191.22 # UK-Hacking site
deny from 108.59.8.80 # hosted-by.leaseweb.com (US-SPAM)
deny from 36.248.160.0/17 # China fujian provincial network (SPAM)
deny from 183.192.0.0/11 # China Mobile Communications (SPAM)
deny from 110.89.37.87 # CHINANET FUJIAN PROVINCE NETWORK (SPAM)
deny from 183.207.228.14 # China-SPAM
deny from 192.151.154.82 # Unknown-SPAM
deny from 192.187.96.0/19 # US - Hacking Site
deny from 212.109.32.11/26 # sovam.net.ua (Ukraine-SPAM)
deny from 46.118.0.0/16 # sovam.net.ua (Ukraine-Hacking site)
deny from 37.115.128.0/17 # broadband.kyivstar.net (Ukraine-Hacking site)
deny from 94.153.0.0/17 # Ukraine - Plugin "WP All Import" Attack site
deny from 109.104.168.81 # Ukraine-Hacking site
deny from 109.108.246.42 # Ukraine-Hacking site
deny from 77.120.121.201 # Ukraine-Hacking site (plasma.co.ua)
deny from 5.248.128.0/17 # 5-248-239-242-broadband.kyivstar.net (SPAM)
deny from 134.249.0.0/16 # 134-249-140-218-gprs.kyivstar.net (SPAM)
deny from 178.137.0.0/16 # kyivstar.net (SPAM)
deny from 195.211.152.0/22 # Ukraine-SPAM
deny from 195.154.188.74 # France-SPAM
deny from 188.163.76.0/24 # sol-fttb.23.76.163.188.sovam.net.ua
deny from 188.163.77.0/24 # sovam.net.ua (Ukraine-SPAM)
deny from 80.93.113.38 # Ukraine-Hacking site
deny from 193.201.224.0/19 # Ukraine-SPAM
deny from 46.151.52.0/22 # Ukraine-SPAM
deny from 31.184.236.0/24 # Latvia-SPAM
deny from 31.193.196.0/24 # Latvia-SPAM
deny from 91.200.12.0/22 # Ukraine-SPAM
deny from 91.207.7.158 # Ukraine-SPAM
deny from 176.36.80.39 # host-176-36-80-39 (Ukraine-SPAM)
deny from 176.109.182.19 # Ukraine-SPAM
deny from 94.22.0.0/20 # Anvia (Finland-BOT)
deny from 114.44.170.172 # Australia-SPAM
deny from 166.62.36.66 # US-Hacking site
deny from 45.59.27.155 # US-SPAM
deny from 104.255.67.238 # US-BOT (VolumeDrive)
deny from 59.115.170.243 # TAIWAN-SPAM
deny from 23.232.143.19 # Unknown-SPAM
deny from 192.240.201.160 # Unknown-SPAM
deny from 118.168.198.179 # Unknown-SPAM
deny from 204.195.139.6 # Unknown-SPAM
deny from 91.214.44.153 # lu-customer-ip.as51430.net
deny from 67.215.237.98 # n6-losangeles-us.samknows.com
deny from 112.175.184.0/24 # Korea - Plugin "Revslider" Attack site
deny from 78.20.76.230 # Germany-Hacking site
deny from 188.40.138.214 # Germany - Plugin "Revslider" Attack site
deny from 3.19.41.74 # Unknown-Hacking site
deny from 23.19.41.74 # Plugin "Revslider" Attack site
deny from 62.210.113.121 # Plugin "Revslider" Attack site
deny from 93.188.165.166 # xmlrpc.php Attack site
deny from 195.220.216.12 # France - xmlrpc.php Attack site
deny from 185.3.32.20 # Unknown-Hacking site
deny from 176.119.109.177 # Unknown-Hacking site
deny from 81.163.119.20 # Unknown-Hacking site
deny from 109.188.124.27 # Russia-Hacking site
deny from 52.10.157.134 # US-Hacking site
deny from 179.43.117.234 # Unknown-Hacking site
deny from 31.193.141.19 # Plugin "Revslider" Attack site
deny from 193.246.63.31 # Switzerland - Plugin "Revslider" Attack site
deny from 91.142.223.95 # Plugin "Revslider" Attack site (Spain)
deny from 91.142.252.91 # Plugin "Revslider" Attack site
deny from 104.148.44.39 # Plugin "FCKEditor for WordPress" Attack site
deny from 80.82.65.82 # Plugin "FCKEditor for WordPress" Attack site
deny from 5.101.156.0/24 # xmlrpc.php Attack site
deny from 5.101.157.0/24 # Russia - Plugin "Revslider" Attack site
deny from 80.237.251.203 # Germany - Plugin "Revslider" Attack site
deny from 211.200.192.54 # Korea - Plugin "Revslider" Attack site
deny from 188.143.232.0/24 # Russia - SPAM (LeonLundberg-net)
deny from 188.143.234.0/24 # Russia - SPAM (ToussaintDesaulniers-net)
deny from 72.18.205.234 # US - Plugin "Revslider" Attack site
deny from 118.170.33.3 # Plugin "MiwoFTP" Attack site
deny from 188.165.0.0/16 # France - Plugin "Revslider" Attack site
deny from 95.110.202.57 # Plugin "Revslider" Attack site
deny from 95.110.232.43 # Plugin "Revslider" Attack site
deny from 92.100.143.41 # Russia-Hacking site
deny from 85.25.109.90 # Germany - Plugin "Revslider" Attack site
deny from 89.130.171.6 # Plugin "Revslider" Attack site
deny from 194.54.160.9 # Russia-Hacking site
deny from 46.241.242.30 # Armenia-Hacking site
deny from 46.200.221.11 # pool.ukrtel.net - Hacking site
deny from 217.69.133.13 # Russia-Hacking site
deny from 37.59.47.101 # France - Plugin "Revslider" Attack site
deny from 91.121.136.67 # France - Hacking site
deny from 162.209.48.30 # Unknown-Hacking site
deny from 112.148.213.96 # Plugin "BackupBuddy" Attack site
deny from 2.132.204.182 # Bitrix Site Manager Attack site
deny from 79.170.44.93 # UK - Plugin "Revslider" Attack site
deny from 182.118.0.0/16 # 中国迷惑BOT (hn.kd.ny.adsl)
deny from 59.173.148.207 # China - Plugin "FCKEditor" Attack site
deny from 171.113.176.0/24 # Plugin "FCKEditor" Attack site
deny from 111.172.99.227 # Plugin "FCKEditor" Attack site
deny from 185.23.21.11 # Transposh Hacking site
deny from 109.197.72.51 # Russia-SPAM
deny from 37.59.0.0/16 # ovh.net France-Hacking site (37.59.1.10)
deny from 213.251.128.0/18 # ovh.net France-Hacking site (213.251.182.110)
deny from 167.114.116.195 # US - Hacking site
deny from 183.60.244.49 # China - Hacking site
deny from 186.202.127.0/24 # Plugin "Revslider" Attack site
# 以下略
With this, the site that was crowded with BOT has become quite quiet. (Lol)
[Access restrictions]
As a result of the access analysis, we found a case where it was impossible for Apache to reverse the IP address to the host name. Therefore, we restricted access not by using the host name but by describing all IP addresses.
As an example, for a BOT that attacks using multiple IP addresses as shown below, the target IPs are set to be rejected collectively by specifying the IP subnet mask.
195-154-188-41.rev.poneytelecom.eu 195.154.188.41 195-154-173-141.rev.poneytelecom.eu 195.154.173.141 195-154-189-155.rev.poneytelecom.eu 195.154.189.155 195-154-191-162.rev.poneytelecom.eu 195.154.191.162 195-154-188-224.rev.poneytelecom.eu 195.154.188.224
[How to specify the subnet mask]
From this point on, information processing technicians can skip this.
Get the server information at the whois database site below for the suspected BOT host name or IP address.
Domain / IP address search [whois information search]
As an example, search for "195.154.188.41".
As a result, the range of IP addresses used by the network can be confirmed as follows.
inetnum: 195.154.128.0 - 195,154,255,255
Expand this into a binary number.
11000011 10011010 10000000 10000000
11000011 10011010 10000000 10000001
11000011 10011010 10000000 10000010
11000011 10011010 10000000 10000011
・
・
・
11000011 10011010 11111111 11111110
11000011 10011010 11111111 11111111
This shows that the upper 17 bits are fixed and the lower 15 bits are variable.
Therefore, the subnet mask for fixing the upper 17 bits can be expressed as follows.
11111111 11111111 10000000 00000000
If the value of the result of logical AND of this subnet mask and binary number matches the target IP address, it is a restricted IP address.
This subnet mask is described in ".htaccess" as follows.
195.154.0.0/17
Or
195.154.0.0/255.255.128.0
Since we haven't eliminated all the bots yet, we have a small bot, but it feels much quieter than before.
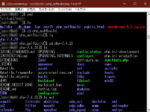
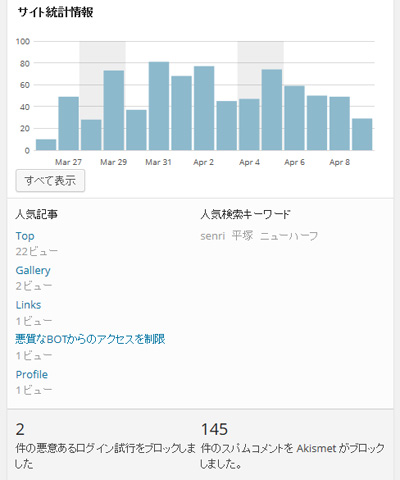
The following is the monitor screen of Perl's access analysis program after restricting BOT access.
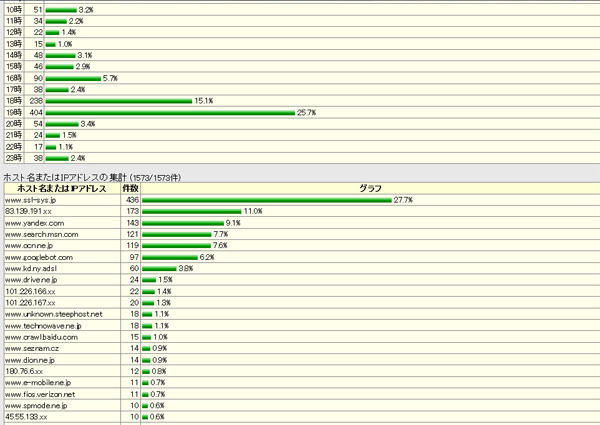
* Added April 9
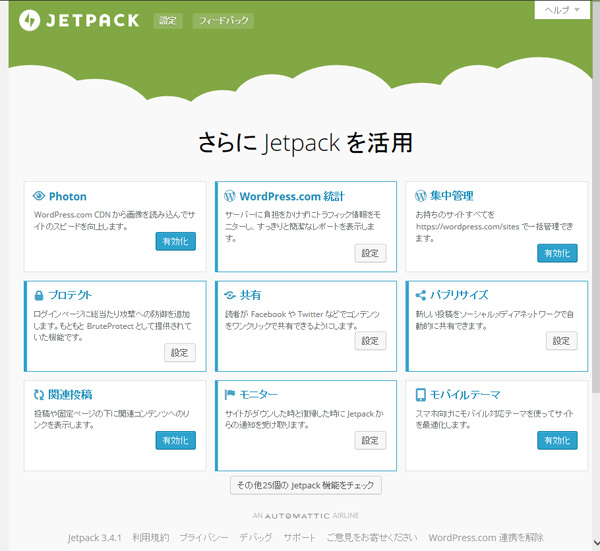
As a precautionary measure, we have also enabled a plug-in "Jetpack-Protect" to protect against brute force attacks on the login screen today.
* Added September 18
The server was down due to a DOS attack from Korea or a SPAM attack from Ukraine the other day, so we updated ".htaccess". The following description is part of it.
deny from 121.160.0.0/11 # Korea DOS Attack Site
deny from 121.189.37.15 # Korea SPAM site
deny from 46.119.121.0/24 # Ukraine SPAM site
deny from 78.137.32.0/19 # Ukraine SPAM site
deny from 93.76.64.0/20 # Ukraine DOS Attack site
deny from 111.172.97.115 # China SPAM site
deny from 111.172.104.138 # China SPAM site
deny from 169.54.143.212 # static.reverse.softlayer.com
deny from 192.0.64.0/18 # US SPAM site
deny from 204.12.241.170 # depictionorganizers.com
deny from 216.244.82.0/24 # tnxe.sessionall.com
In robots.txt, access from the annoying BOT is denied as follows.
By the way, Steeler and Shim-Crawler are crawlers from the laboratory of the University of Tokyo.
User-agent: Yandex
Disallow: /
User-agent: baiduspider
Disallow: /
User-agent: BaiduMobaider
Disallow: /
User-agent: BaiduImagespider
Disallow: /
User-agent: MJ12bot
Disallow: /
User-agent: AhrefsBot
Disallow: /
User-agent: BLEXBot
Disallow: /
User-agent: SemrushBot
Disallow: /
User-agent: LSSRocketCrawler
Disallow: /
User-agent: LinqiaScrapeBot
Disallow: /
User-agent: Wotbox
Disallow: /
User-agent: Steeler
Disallow: /
User-agent: Shim-Crawler
Disallow: /
User-agent: bingbot
Crawl-delay: 5
* Added September 26
From the analysis of the access log, we confirmed that there was evidence of a DDOS attack using the pingback function of WordPress, so we disabled the pingback function of this site.
Reference article is here ⇒ Alert: Request for measures against DDoS attacks that abuse WordPress features
Disable the pingback function by installing the plug-in "Disable XML-RPC Pingback", add the following definition to ".htaccess", and prohibit access to the remote posting program "xmlrpc.php" Did.*
* 2020.4.1 Addendum
When the following definition and the plug-in "Disable XML-RPC Pingback" are enabled, the connection between Jetpack and WordPress is broken, and "Fatal problem (Error 200)" is displayed in Jetpack site health status. It becomes.
<Files xmlrpc.php>
Order Deny,Allow
Deny from all
</Files>
2018.04.10 Addendum
There was a large amount of spam access using Amazon's AWS, and even if it was denied with an IP address, it came persistently with another IP address, so we denied access by specifying a domain as follows.
order deny,allow
allow from all
deny from amazonaws.com
2020.05.11 update
Since we are denying access from Amazon's AWS, we have been unable to access some crawlers and websites, which hinders site operation, so I'm currently releasing access restrictions to amazonaws.com.
2023.03.06 Added
For enhanced security, we currently install and operate the following iThemes Security plugins.
iThemes Security offers brute force attacks, banned user settings, lockout, site scanning, two-factor authentication (2FA), permanent blocking of repeat offenders, file modification detection, and many other security features.